Home
Explanation
Anonymizer
RFID Voting
Tools
Contact

UNDER DEVELOPMENT ae Expert Plan
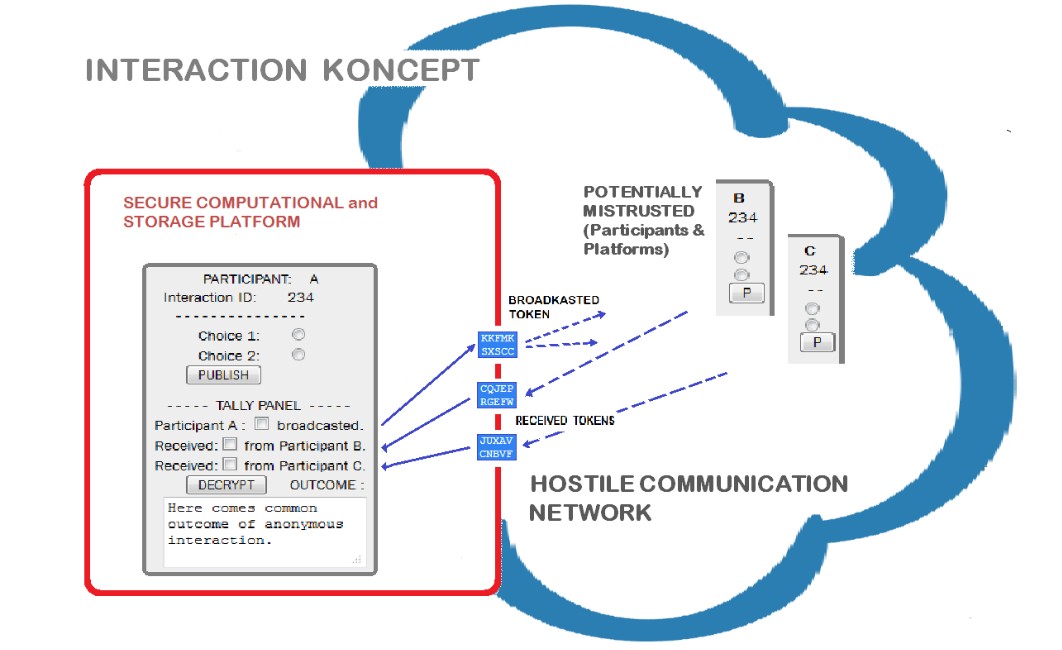
ANONYMOUS interaction for COLLECTIVE outcome with VERIFIABILITY
A process where everyone can interact by broadcasting tokens (as conditional commitments), and at the end, everyone must undisputedly agree on quantifiable collective outcome, and no-one should know which way anyone else intentions was.
- Anonymity is assurance that identity of message originator is protected although the message itself can be traced back to originator. This is, because once the semantic pay-load (or impact knowledge which message carry) toward overall outcome is decoupled from the meta-content of message, we have no more visibility from which source this impact comes. This is accomplished by surjective one-way cryptographic construction. ....
- Verifiability is assurance that the message is quantifiable implemented as intended in application at destination point. Enables participant to initiate revocation on time if necessary. ...more.
- Participant's interaction is exchange of conditional commitments in response to published agenda identified by unique ID number. This is the same as in-person conditionally signing on paper written contract among participants with mandatory specified contract performances on the distance over the network. The concept of “smart contract” can easily be implemented because contract execution can be triggered in real time by automated process which evaluates received tokens to generate transaction outcome events.
- HOSTILE COMMUNICATION NETWORK is where adversary may alter content, create new, or stop message from propagating across.
- SECURE COMPUTATIONAL and STORAGE PLATFORM is environment where participant can use previously stored tokens as coded message to broadcast his choice to other participants. Where he can determine common outcome based on his unaltered coded message and received coded messages from other participants. He can verify correctness of outcome by using the same publicly known process in his privacy but using his different choice without broadcasting it over the network. Participant can maintain his anonymity if he publishes only one choice from his secured storage regardless of hostile network or distrusted others .
- POTENTIALLY MISTRUSTED (Participants & Platforms) are participants (or unauthorized adversaries using platforms and impersonating legitimate participants) with capabilities to share content, modify and create new messages on individual or conspirator manner.
- TOKENS or coded segments are in essence conditional commitments toward outcome in common application. Only token combination which correspond to set of actual events is legitimate and create cipher with integrity. By finding and decrypting this combination the quantified outcome can be determined.
Generation and distribution of tokens should be done at "anonymization ceremony". The key for anonymity is that no-one has knowledge of all distributed tokens among all participants. Reuse of the tokens may result in diminishing of absolute anonymity of participants.
|
|
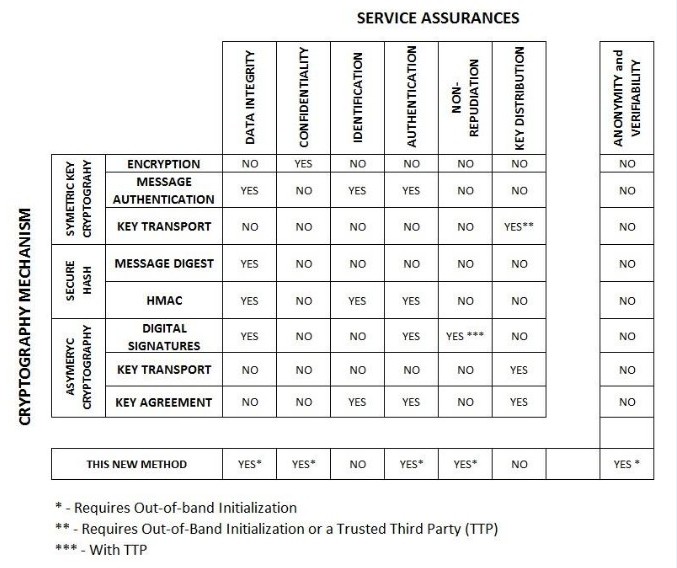 |
Most Anonymity assurance providers will not program up their own custom application, but will instead select a “boilerplate” application off the shelf and fill in the blanks using application construction kit.